A recent phishing campaign against targets in France used Chocolatey to install software on the target computers. There has been clickbait headlines, speculation and incorrect suggestions to the use of Chocolatey in this attack that I wanted to provide a response for reassurance of our customers and community.
What Happened?
On March 21, 2022, Proofpoint “observed new, targeted activity impacting French entities in the construction and government sectors” that “used macro-enabled Microsoft Word documents to distribute the Chocolatey installer package”. You can find the full article on the Proofpoint website.
The key points in the article that involve Chocolatey are:
- Chocolatey is installed.
- Chocolatey is used to install the
pythonpackage which also installspip.
How Did The Attack Work
The steps are outlined in the Proofpoint article.
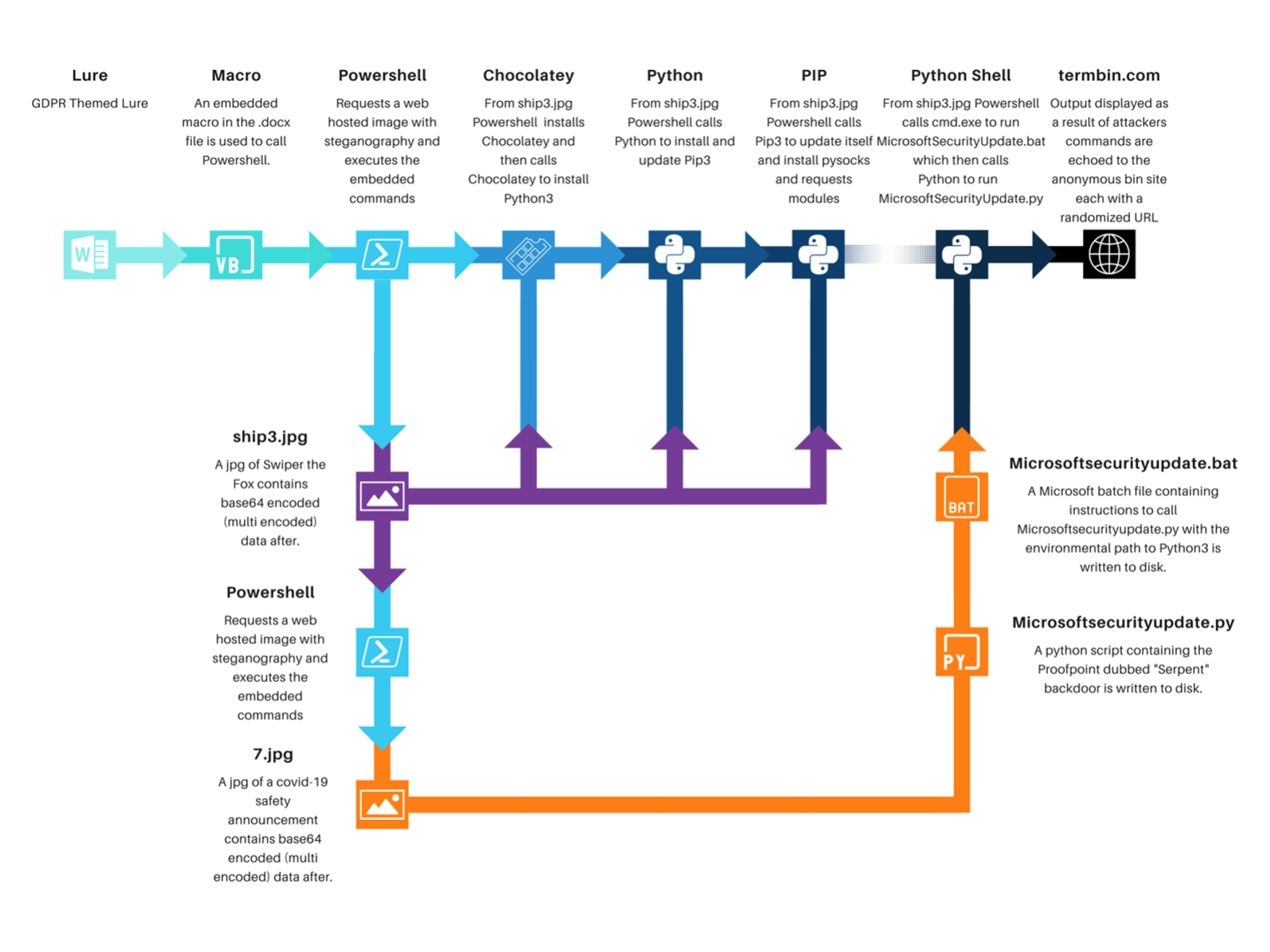
Serpent Infection Chain (Proofpoint)
For the attack to be successful:
- Macros must have been permitted to run on the targeted computer (in modern versions of Microsoft Office these are disabled by default).
- The PowerShell script that is used to install Chocolatey must have been permitted to run with Administrator privileges.
Without both of those requirements, Chocolatey would not have been installed. And the python package, and pip, would not have been installed.
If you’ve installed Chocolatey before you’ll know that you need Administrator privileges to do that. If you don’t have those privileges, Chocolatey simply won’t install. And in that case the attack would fail.
Providing Clarity
Some reports have provided inaccurate or misleading information and I wanted to address those here.
Evade Detection
The Proofpoint article says:
“Chocolatey is also being used to evade detection by security software as it is commonly used in enterprise environments to manage software remotely and could be on an allowed list in IT environments.”
Chocolatey doesn’t evade detection by any security software. In some environments, the IT Team have prevented all software by default from running and add the software that is allowed to run to a whitelist. What is being suggested here is that because Chocolatey is popular in enterprise environments, it may have been added to those whitelists.
While Proofpoint are not suggesting that Chocolatey is evading detection, I can understand how it might be read that way.
Abuse Of Chocolatey
In some reports it’s been mentioned that installing Chocolatey, python and pip, is an abuse of Chocolatey. Both Python and PIP are also used as is PowerShell, but none of those have been described as being abused. Chocolatey is just being used to install software, which is what Chocolatey was designed to do. It’s worth noting that the Proofpoint article points out that the use of Chocolatey is used legitimately to install Python and PIP and then the script runs something malicious.
Chocolatey itself is installed from the Chocolatey Community Repository at a rate of 35K installs per hour, so we spoke with Proofpoint to see if there was anything special about the requests that we could target to help prevent or slow down this attack. Unfortunately the script that is run is installing Chocolatey like everything else.
Questions From Our Customers and Community
Chocolatey takes security seriously. We appreciate that while we know and understand that this attack simply used Chocolatey in the way it is used hundreds of thousands of times per day, our customers and community may not. I wanted to address some questions that have been asked.
Was Chocolatey exploited for this attack?
No, Chocolatey was not exploited for this attack. Chocolatey was used to install a legitimate package, (python), from the Chocolatey Community Repository.
Was a package infected?
No. The python package has a total of 10.5M downloads with the latest stable version having almost 117k downloads since it was released on March 16. The package was scanned by 50 to 60 AV engines using Virus Total with no detections.
Was Chocolatey used to install backdoors?
No. Chocolatey was used to install a legitimate package, (python), from the Chocolatey Community Repository.
Recommendations
The recommendations I make below are not new, but it is always important to reinforce them whenever possible:
- We would recommend that people pause when a UAC prompt is raised on a computer if they opened something (Microsoft Word) that would not normally require elevation.
- Your regular login does not have Administrator privileges. If an Administrator privileged account is needed, use a secondary account that is only used for the administrative tasks.
- Turn off macros in Microsoft Office. Newer versions already have it turned off by default.
Summary
It’s understandable that our customers and community will be concerned when issues such as these surface. I hope this clears up the confusion and misinformation that has surfaced recently.
For Security related issues, please see our documentation for responsible disclosure. If you are a licensed Customer with valid Maintenance and Support, then please do reach out to Support (run choco support to find out your options) or use our Community Discord Chat.
